![[JoGu]](../../JGU.gif) |
CryptologyAnalysis of Periods after KASISKI |
|
![[JoGu]](../../JGU.gif) |
CryptologyAnalysis of Periods after KASISKI |
|
Already in the 16th Century PORTA and the ARGENTIs occasionally broke polyalphabetic encryptions by
An attack with known plaintext is
The attack with known plaintext was propagated by KERCKHOFFS, together with his method of »symmetry of position« that works for dependent secondary alphabets. This approach apparently was known to BABBAGE as early as 1846, but he never got around to publish it.
Source: O. I. Franksen: Babbage and cryptology. Or the mystery of Admiral Beaufort's cipher. Math. Comput. Simul. 35/4 (1993), 327–367, Abstract.
In World War I the British Navy used the GRONSFELD cipher (among others), that is a BELLASO cipher with shifts of at most nine letters. The key is given by a sequence of some decimal digits that are periodically repeated. The Mathematician Ludwig Föppl who served as radio operator in the German Army observed that a certain group of 18 letters occurred frequently in British radio messages. He supposed this to be a standard phrase, and had success after trying »What is your position?« even without in advance knowing the type of cipher used.
Exercise. Determine the key under the assumption that Pöppel observed the ciphertext AIGYL UCPAW SQWJZ NRP.
Source: Hilmar-Detlef Brückner: Germany's first Cryptanalysis on the western front: Decrypting british and french naval ciphers in World War I. Cryptologia 29 (2005), 1–22.
Attack on short »Vigenère« ciphertexts:
Tobias Schrödel: Breaking short Vigenère ciphers. Cryptologia 32 (2008), 334–347.
[F. W. KASISIKI, Prussian Major, 1805–1881]
In step 3, that is in cryptanalyzing the monoalphabetically encrypted columns, we face the complication that the columns don't represent connected meaningful texts. Pattern search is pointless. However frequency analysis makes sense.
There are some simplifications for dependent alphabets:
Especially simple is the situation with BELLASO's cipher, as soon as the period is known: Each column is CAESAR encrypted. Therefore we need to identify only one plaintext letter in each column.
Three approaches to determining the period of a periodic polyalphabetic cipher are
KASISKI in 1863 published his method and thereby immediately demolished the belief in the security of periodic polyalphabetic ciphers.
[PORTA in a single case already had used this method, but never thought of a systematic approach. BABBAGE (1791–1871) had found the method ten years earlier than KASISKI's publication but never published it and didn't influence the developement of Cryptology. Therefore it is appropriate to credit the method to KASISKI.]
In contrast to the exhaustion approach the other two methods immediately identify the situation where there is no period.
![[Repetition]](Repetition.gif)
We start with three observations:
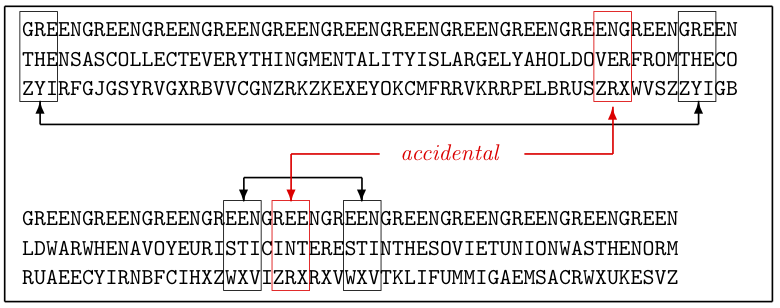
An assessment of this probability is related to the birthday paradox of probability theory, and is contained in the appendix of this chapter. It was published in
K. Pommerening: Kasiski's Test: Couldn't the repetitions be by accident? Cryptologia 30 (2006), 346-352.
A Perl program that searches for repetitions is here. It may be called online by a web form.
Exercise. Search for repetitions in one of the formerly generated polyaphabetic ciphertexts.